注:本议题公开发布于CSOP-2023(北京站)。
议题演讲材料下载:安全小飞侠_CSOP 2023北京站_云上攻防的点-线-面-体
本文主要是记录笔者基于近期对云上攻防态势的分析思考和展望云服务安全架构设计框架的未来发展趋势,观点仅代表个人。
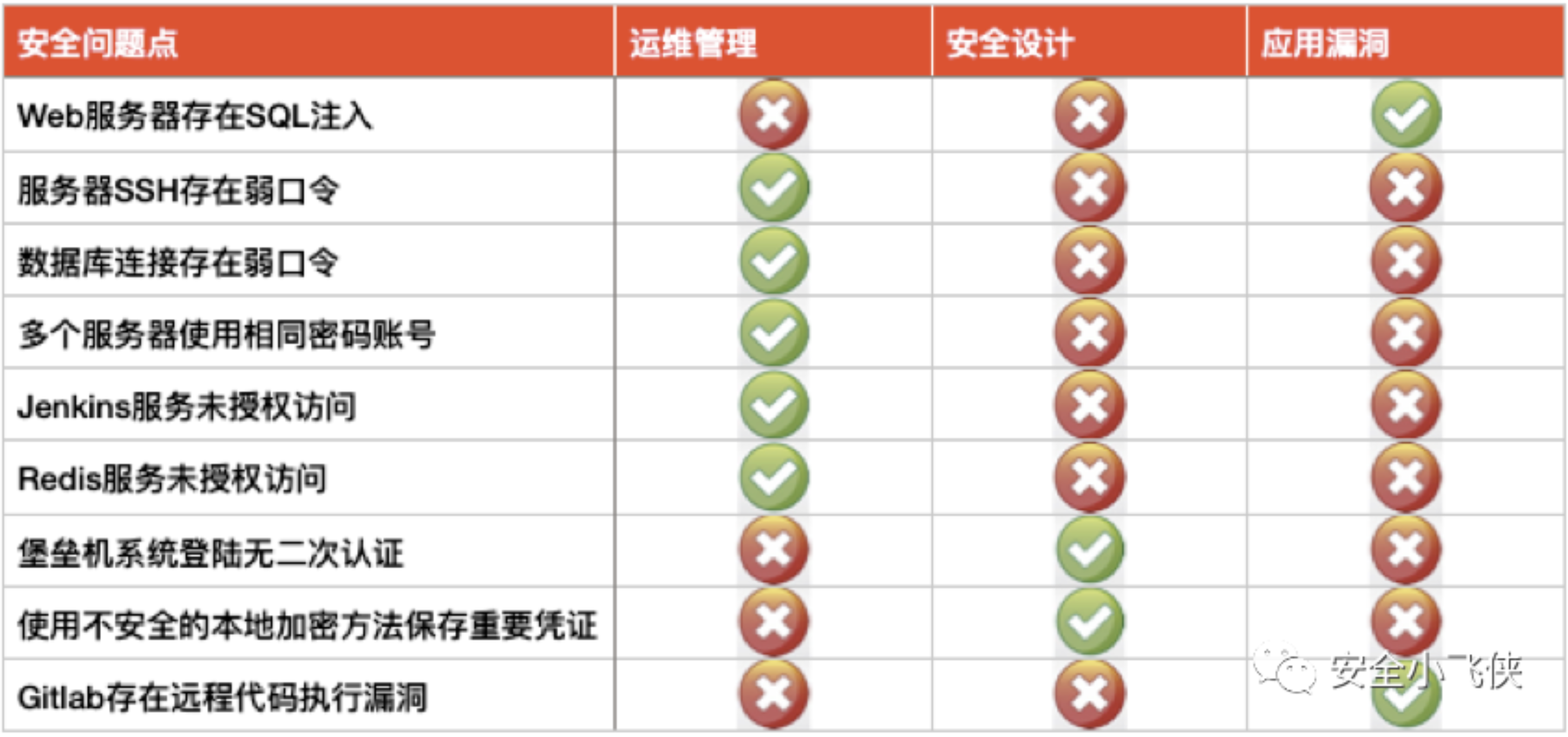
近期,笔者详细分析了近几年所有公开的云厂商漏洞报告[1]发现,头部云厂商的云服务都存在不少漏洞,其中AWS、GCP、Azure被公开披露的云服务漏洞最多。
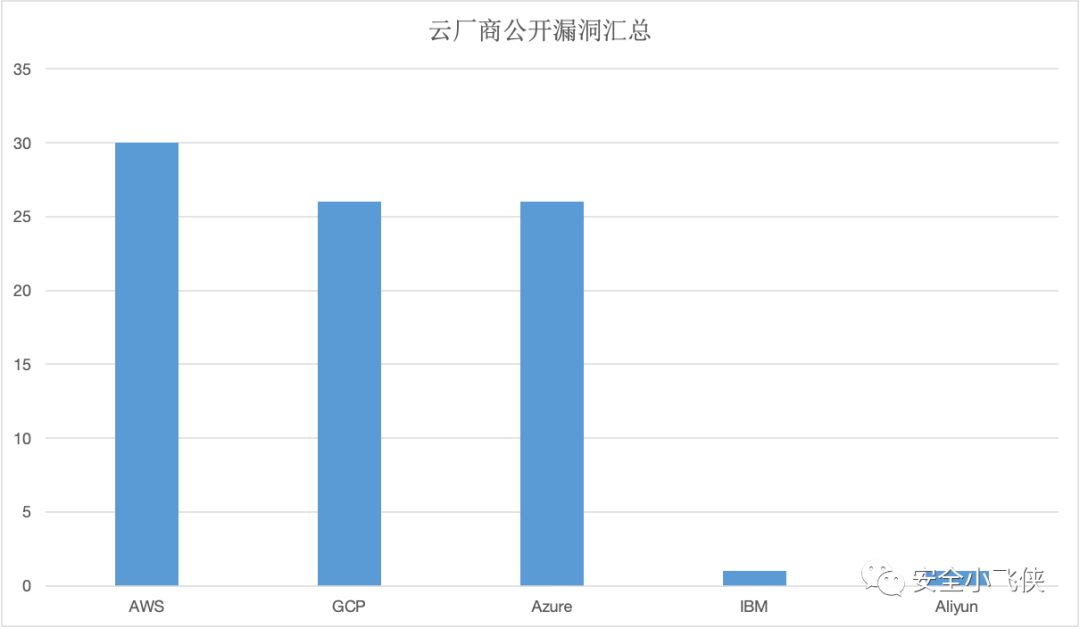
由此可见,大量基于k8s/容器等新技术构建的云服务是攻击者/安全研究者最青睐的攻击/研究对象,其次就是近年来针对基于开源数据库软件构建的云数据库和数据管理服务的攻击趋势明显上升,此外针对CI/CD云服务的供应链攻击也在显著增多,还有针对最常见的云上IAM服务的攻击依然普遍存在。
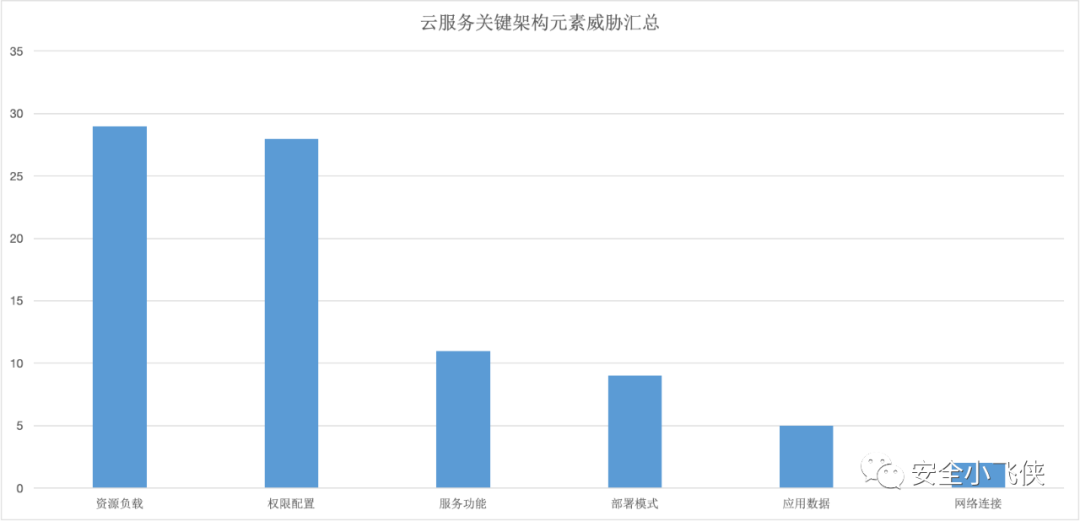
通过分析以上针对云服务的攻击类型可以总结出云服务面临的主要威胁类型(STRIDE)如下所示:
根据识别出来的云服务面临的主要威胁,站在云服务安全架构设计的角度来看导致这些安全威胁的根因应该包括以下几个方面:
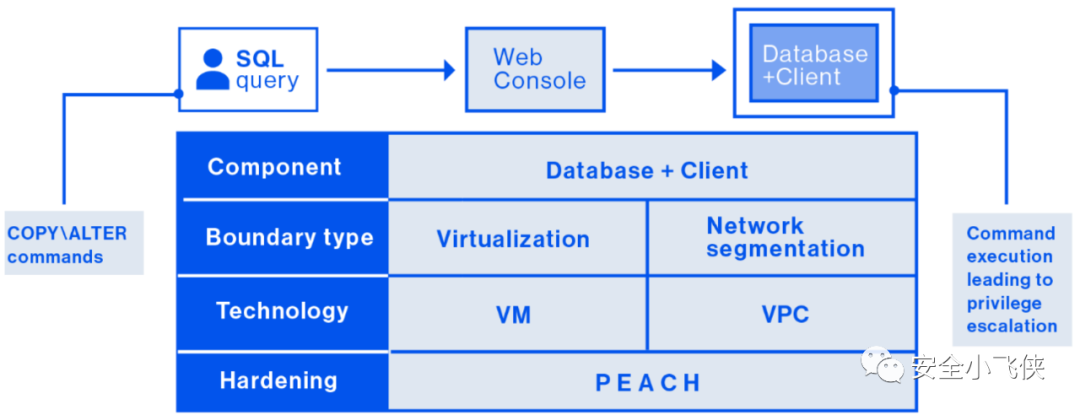
云安全公司Wiz近期发布了一个专门针对云服务租户隔离框架PEACH,结合其在云安全领域的研究成果系统地提出了云服务安全架构设计方法论[3]。
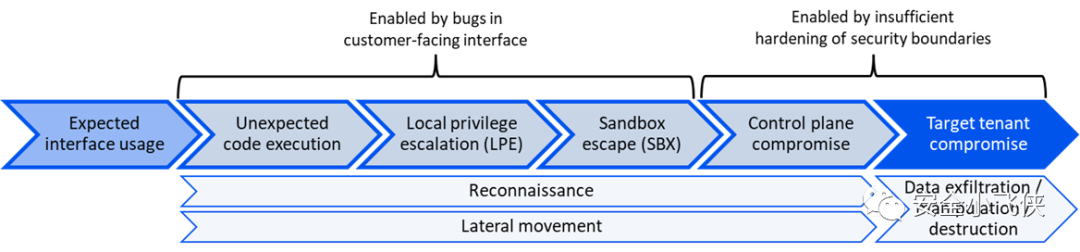
具体分两步走:
第一步,对云服务应用进行威胁建模
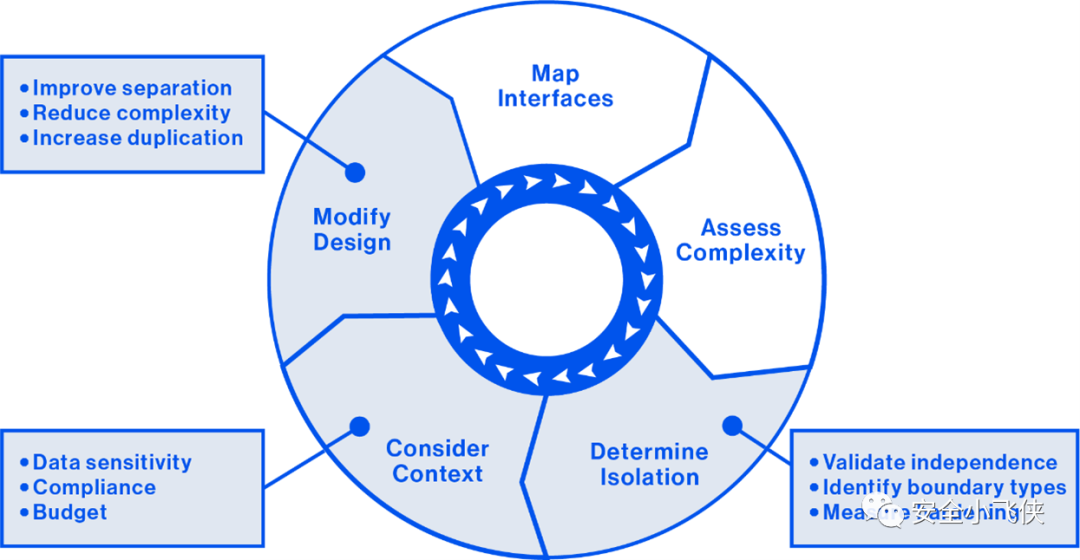
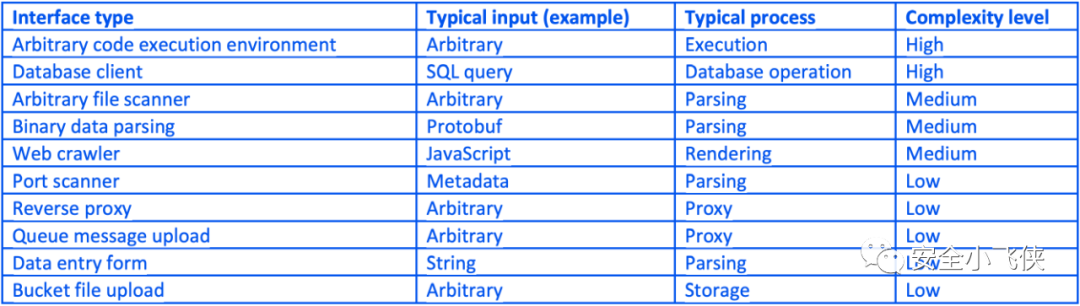
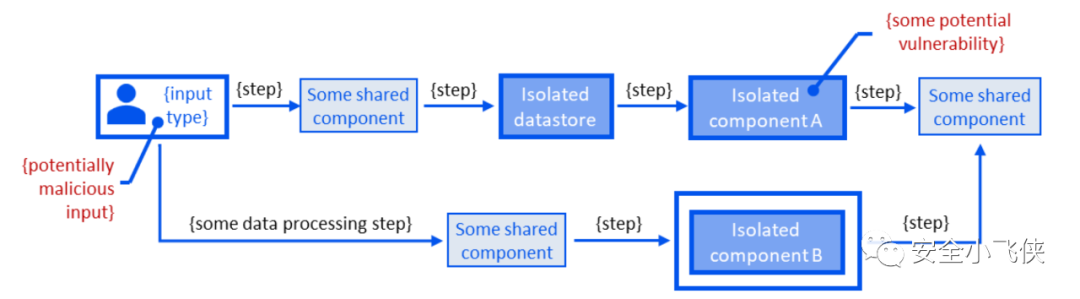
2.7) 如果隔离级别在复杂性和情境因素(包括合规性、数据敏感度和预算考虑)方面被确定为不足,则根据需要修改设计,通过减少复杂性,增强隔离性,增加资源冗余度来提高隔离级别。
第二步,基于P.E.A.C.H.五个方面实施云服务安全加固
应该说PEACH框架是一个不错的云服务安全架构设计框架,但是细究下来也存在一些不足:
因此,结合云上攻防态势分析的结果和PEACH框架的核心思想,笔者提出了一种新型的云服务安全架构设计框架(LSSA)。
第二步,针对每一个关键架构元素进行风险识别和安全加固

本系列文章将分为几篇介绍一下态势感知的发展历程和行业实践。
态势感知的概念起源于军事理论,早在春秋时期著名的兵书《孙子兵法》中就有提到“知己知彼、百战不殆”,这估计也是最早把对敌情态势的感知作为克敌制胜的关键因素的观点了。
第一次世界大战期间“空战之父”德国的王牌飞行员Oswald Boelcke也曾经提到类似的说法:
the importance of gaining an awareness of the enemy before the enemy gained a similar awareness, and devised methods for accomplishing this.(先敌一步掌握对方的态势并设计出相应的实现方法至关重要)
第二次世界大战期间德国空军飞行员Erich Alfred Hartmann发明了著名的SDAR空战战术理论(即See-Decide-Attack-Reverse),首先通过观察敌人决定如何继续攻击,然后才进行正式攻击,接着脱离接触并重新评估局势进行下一轮的观察。
越南战争期间美国空军上校John Boyd结合空战中的经验和教训总结形成了著名的OODA模型(即Observe-Orient-Decide-Act),通过观察、调整、决定、行动,反复推进并以此形成循环,该模型在美国空军中获得迅速推广。
1995年前美国空军首席科学家Mica Endsley仿照人类的认知过程建立并结合空军战术理论正式发表了关于“态势感知”的第一个理论模型(Endsley模型),该模型将态势感知分为三个阶段,即态势感知、态势理解、态势预测。此后,态势感知开始广泛应用于医疗救援、交通、航空、执法、网络安全等其他领域。
随着计算机网络的发展以及网络安全复杂性的凸显,“网络安全态势感知(Cyber Security Situation Awareness,CSSA)”也越来越得到重视并逐渐成为网络安全领域不可或缺的重要组成部分之一。如今,比较主流的网络安全态势感知的定义主要来自于Endsley提出的,即态势感知是对目标网络空间中的安全威胁进行感知,应用适当的评估、评价、推理分析机制理解攻击意图,并以此预测未来的安全态势。
有了以上对态势感知发展历程和主流定义的基本了解,可以通过几个行业实践来深入理解一下如何构建网络安全态势感知体系。
导读:美国国家态势感知体系以管治为核心,以各自构建、独立管理、信息共享、统一协调、常态化呈现为策略。
美国国家态势感知体系主要由国土安全部(DHS/CISA)负责的联邦政府网络态势感知体系和国家安全局(NSA/CSS)负责的军事网络态势感知体系构成,两者独立构建和运作,但通过情报共享机制由国家情报总监办公室(ODNI)协调汇总所有情报机构的态势信息生成总统每日内参(PDB)提交给美国总统和少数政府高层官员作为国家战略决策的重要输入之一。
国土安全部通过国家网络空间安全保护系统(NPS),也称ENISTEIN系统,构建了联邦政府的网络态势感知体系。
导读:欧洲金融行业态势感知体系以市场驱动为核心,以构建统一的威胁情报共享计划为策略。
欧洲通过建立市场驱动的泛欧金融基础设施欧洲网络韧性委员会(ECRB)的网络信息和情报共享计划(CIISI-EU)构建了泛欧金融行业的态势感知和威胁情报共享体系。
本文主要是对美国商务部工业和安全局(BIS)于2022年5月26日发布的《Information Security Controls: Cybersecurity Items》的详细解读及该细则发布后对中国政府和企业的影响分析。
1996年7月,在美国的主导下以西方国家为主的33个国家在奥地利维也纳签署了《瓦森纳协定》(简称“瓦协”Wassenaar Arrangement),决定从1996年11月1日起实施新的控制清单和信息交换规则。其中包含两份控制清单:一份是军民两用商品和技术清单,涵盖了先进材料、材料处理、电子器件、计算机、电信与信息安全、传感与激光、导航与航空电子仪器、船舶与海事设备、推进系统等9大类;另一份是军品清单,涵盖了各类武器弹药、设备及作战平台等共22类。
2004年,美国商务部工业和安全局(BIS)发布了出口管制条例(EAR)的许可例外的国家分组的附件《Supplement No.1 to Part 740-COUNTRY GROUPS》,第一次将中国(China(PRC))列为D:1(国家安全)、D:3(生物化学)、D:4(导弹技术)组中,从而限制涉及国家安全、生物化学、导弹技术领域的商品或技术出口到中国。
2013年,《瓦森纳协定》将网络安全条目纳入出口管制的范围之中,其中包含了对“入侵软件”的定义,具体包括:
2014年,BIS刷新了出口管制条例(EAR)的许可例外的国家分组的附件《Supplement No.1 to Part 740-COUNTRY GROUPS》,开始将中国也列为D:5(美国武器禁运国家)组中。
2015年5月20日,BIS针对《瓦森纳协定》中关于网络安全条目的出口管制规定的适配和对于美国工业界的影响发布了建议规则,并公开向美国各界征求意见。
2017年12月,经过美国的提议和协商《瓦森纳协定》综合了美国各界的反馈建议和BIS的建议规则最终同意了对原先的网络安全条目的出口管制项做了部分调整和修正,具体体现在三个方面:
2018年8月13日,美国总统签署生效了《出口控制改革法案》(ECRA),从法律上赋予了BIS发布和维护《信息安全管控:网络安全条目》细则的权力。
2021年10月21日,BIS基于2017年《瓦森纳协定》中关于网络安全条目的出口管制项的修正结论,发布了《信息安全管控:网络安全条目》细则暂行版建立了一个新的许可例外即授权网络安全出口许可例外(ACE)并向美国各界征求意见,并计划2022年1月19日生效。
2022年1月12日,BIS根据美国各界对《信息安全管控:网络安全条目》细则暂行版的反馈建议延迟其生效时间至2022年3月7日,并同意提供额外的细则实施指导和FAQ。
2022年5月26日,BIS发布了《信息安全管控:网络安全条目》细则最终版并生效执行。
授权网络安全出口许可例外(ACE)授权本节(b)段规定的“网络安全条目”的出口、再出口和转让(国内),包括视为出口和再出口,但须受本节(c)段规定的约束。
本许可例外下被视为出口和再出口的物项均需要被授权,但本节第(c)(1)段所述的被视为向E:1和E:2组的国家,及本节(c)(2)段所述的某些“政府最终用户”,并受本节(c)(4)段所述的最终用途限制的约束的出口或再出口除外。即使ACE不适用于某些特定场景,其他许可例外也可能适用。例如,许可例外GOV(第740.11节)授权向美国政府机构和人员出口某些产品;许可例外TMP(第740.9(a)(1)条)授权在某些情况下出口、再出口和转让(在国家)贸易工具。
以下术语和定义仅用于授权网络安全出口许可例外(ACE)。
(1)网络安全条目(Cybersecurity Items):是ECCN 4A005、4D001.a(用于4A005或4D004)、4D004、4E001.a(用于4A005、4D001.a (用于4A005或4D004)或4D004), 4E001.c、5A001.j、5B001.a(用于5A001.j)、5D001.a(用于5A001.j),5D001.c(用于5A001.j或5B001.a (用于5A001.j))和5E001.a(用于5A001.j或5D001.a (用于5A001.j))。
(2)数字组件(Digital Artifacts):是在信息系统上被找到或发现的条目(例如,“软件”或“技术”),这些条目可以显示与该信息系统的使用、危害或其他影响有关的过去或现在行为。
(3)最惠待遇网络安全最终用户
具体包括:
(i)美国子公司;
(ii)银行和其他金融服务提供者;
(iii)保险公司;
(iv)提供医疗或以其他方式进行医学实践的民间卫生和医疗机构,包括医学研究。
(4)政府最终用
就本节而言,主要是指提供任何政府职能或服务的国家、区域或地方部门、机构或实体,包括代表该实体行事的实体或个人。本术语不包括本节第(b)(3)段中列出的任何“最惠待遇网络安全最终用户”。此术语包括但不限于:
(i)国际政府组织;
(ii)政府经营的研究机构;
(iii)高敏感政府最终用户;
(iv)低敏感政府最终用户;
(v)完全或部分由政府或政府授权机构的所经营或拥有的公共事业机构(包括电信服务提供商和互联网服务提供商);
(vi)完全或部分由政府或政府授权机构的所经营或拥有的交通枢纽和服务(例如:航空公司和机场、船舶和港口、铁路和火车站、公共汽车、卡车和公路);
(vii)完全或部分由政府或政府授权机构的所经营或拥有的涉及制造、分销,或提供《瓦塞纳协定》军用清单中规定的物品或服务的零售或批发公司。
(5)就本条而言,“部分由政府或政府授权机构经营或拥有”是指外国政府或政府授权机构实际拥有或控制(直接或间接)外国实体25%或更多的有表决权证券,或外国政府或政府授权机构有权任命外国实体董事会过半数的董事成员。
授权网络安全出口许可例外(ACE)不授权以下场景中的“网络安全条目”的出口和再出口、或(国内)转让:
(1)出口至《Supplement No.1 to Part 740-COUNTRY GROUPS》国家分组清单中的E:1或E:2组的国家。
(2)出口至《Supplement No.1 to Part 740-COUNTRY GROUPS》国家分组清单中的D:1、D:2、D:3、D:4或者D:5组的国家的“政府最终用户”,但是排除以下的情况:
(i)数字组件(Digital Artifacts)(特指与涉及由“最惠待遇网络安全最终用户”拥有或运营的信息系统的网络安全事件有关的数字组件),向同时列在D组和A:6组的国家的警察或者司法机构提供用于刑事或民事调查或起诉的网络安全事件;
(ii)“网络安全条目”,向同时列在D组和A:6组的国家的国家计算机安全事件应急响应小组提供用于应对网络安全事件、“漏洞披露”,或用于刑事或民事调查或起诉的网络安全事件。
(3)本节(c)(1)和(c)(2)段中的约束也适用于与“漏洞披露”和“网络事件响应”有关的活动,包括出口、再出口和转让(国内)。
注解:就本节(c)(1)和(c)(2)而言,ECCN 4E001.a和4E001.c中已经排除了“漏洞披露”和“网络事件响应”。
(4)出口至《Supplement No.1 to Part 740-COUNTRY GROUPS》国家分组清单中的D:1组或D:5组国家的“非政府最终用户”,但是排除以下的情况:
(i)向任何“最惠待遇网络安全最终用户”提供ECCN 4A005、4D001.a(适用于4A005或4D004)、4D004、4E001.a(适用于4A005, 4D001.a (适用于4A005或4D004)或4D004)和4E001.c中定义的“网络安全条目”。
(ii)“漏洞披露”或“网络事件响应”。
(iii)被视为出口。
(5)如果出口商、再出口商或转售商在出口、再出口或转让(国内)时“知道”或“有理由知道”(包括视为出口和再出口)”网络安全条目”将用于在未经信息系统所有者、经营者或管理员(包括此类系统内的信息和流程)授权的情况下影响信息或信息系统的机密性、完整性或可用性。
导读:对中国政府最终用户及中国非政府最终用户的影响分析
根据BIS在2022年5月26日发布的《信息安全管控:网络安全条目》细则最终版中描述的授权网络安全出口许可例外(ACE),可以整理出以下的ACE例外的申请流程和典型应用场景。
从以上分析可知,自2022年5月26日起,对中国政府最终用户及中国非政府最终用户的影响主要体现在以下几个方面:
从BIS的出口管制条例实施的历史背景可以看出,BIS早在2004年和2014年就分别将中国加入了D:1、D:3、D:4及D:5组的国家分组中并实施严格的出口管制;此次细则的发布其实是对自2013年《瓦森纳协定》将网络安全条目纳入出口管制的范围之中以来对美国工业界出口所造成的负面影响和合规成本上升后的一定程度上的松绑和微调,以及对执行过程中一些模糊问题的明确、调整和修正。实际上,并没有看出明显的针对中国的进一步出口管制制裁。
参见上文中的分析,涉及“入侵软件”的“网络安全条目”或“数字组件”定义中的软件和技术,中国政府将无法直接获得美国软件供应商的漏洞披露以及网络事件响应相关的信息,但是中国非政府企业仍旧可以直接获取来自于美国软件供应商的漏洞披露以及网络事件响应相关的信息;此外,对于非“入侵软件”的基础软件的漏洞信息暂无影响。
纵观BIS细则全文和历史脉络,该细则并没有涉及基础软件的更新和升级,只是明确强调了在“入侵软件”的生成、命令与控制、交付技术中,仅用于提供基础软件的更新与升级可被出口管制豁免。也就是说,中国政府和企业正在使用的非“入侵软件”的基础软件(如Windows、office、oracle等)的正常更新和升级不在该细则的管控范围内,因此暂时不受任何影响。
对于已被列入实体清单中的中国非政府企业会存在一定的影响,因为BIS在2022年5月26日发布的《信息安全管控:网络安全条目》细则最终版优先遵从实体清单的管控要求。
对于暂未被列入实体清单中的中国非政府企业在获取海外安全研究者或公司的漏洞信息或网络安全事件响应信息暂无影响。
The Category 4 ‘cybersecurity items’ related to “intrusion software” (which is defined in Section 772.1 of the EAR) are identified by the following ECCNs, summarized as follows:
Meanwhile, the Category 5 – Part 1 ‘cybersecurity items’ related to IP network communications surveillance are identified by the following ECCNs, summarized as follows:
最近几年随着软件供应链攻击和数据安全事件的频繁出现,企业面临着重大的软件供应链安全和数据泄露风险,这间接促使了越来越多的企业开始关注DevSecOps,并且期望借此来解决相关的安全风险。
在开始今天的分享之前,先简单介绍一下DevSecOps的定义,这里主要采用援引于DoD(美国国防部)的一段定义,即DevSecOps实际上是一种旨在统一软件开发、安全、运维运营的有组织的软件工程文化和实践。
DevSecOps is an organizational software engineering culture and practice that aims at unifying software development (Dev), security (Sec) and operations (Ops).
由于DevSecOps理念是将安全防御思维贯穿到整个软件开发和运维运营阶段,这就使得DevSecOps体系的构建变成一个可能的解决数据安全和供应链安全的有效途径。今天的这篇文章主要来谈谈大型互联网企业DevSecOps体系构建的总结和思考,为了方便读者理解笔者将会以一个虚拟的公司Parana来做说明。
导读:正如DoD的定义中所讲,DevSecOps不是指具体的技术或者工具平台而是一种软件工程文化和实践,因此对于期望构建DevSecOps体系的企业来说首先需要建设这样的组织和文化。
早在2002年Parana公司的创始人就开始在全公司top-down推广SOA(service-oritented architecture)文化[1]:
此外,Parana公司的理念是Two-Pizza团队[2],即每个团队是一个不超过两个Pizza可以喂饱人数的最小独立组织。团队越小,协作越好。而协作非常重要,因为软件发布的速度比以往任何时候都快。团队交付软件的能力可能是组织在竞争中脱颖而出的一个因素。设想一下需要发布新产品功能或需要修复错误的情况,往往都希望这尽快发生,这样就可以有更短的上市时间。 这样的理念在某种意义上也非常契合DevSecOps的内在逻辑,每个应用的开发运维运营团队应该是一个整体而不是割裂的组织,这样既减少了跨组织间的沟通成本也大大提升了软件交付的敏捷性及软件运行的安全性。
通过在公司top-down推行SOA企业文化和Two-Pizza团队组织形态,Parana公司具备了构建DevSecOps体系的基础,每个Two-Pizza团队类似于军队中的最小作战单元(班),“麻雀虽小但五脏俱全”,每个团队中基本上都配备了以下角色。
导读:有了相应的组织和文化,接下来就是如何通过流程和工具将DevSecOps的理念固化下来,并持续运作。本节将从计划、开发、编译与测试、发布与交付、部署与运维、监控与反馈几个阶段进行介绍。
Parana公司在计划阶段要求每个软件项目立项后需要在应用服务安全评估系统中进行注册,该系统会根据《数据分类分级要求》、《数据分级处理标准》、《TOP威胁风险库》等生成应用服务风险评估问卷,通过回答问卷系统会自动根据问卷结果生成应用服务等级(Red、Orange、Yellow、Green),不同的级别对应着不同的安全要求,如:
对于威胁建模能力的构建,Parana公司建立了安全BP威胁评估培训与分层授权(Security Certifier Training)机制。简而言之,就是在每个业务研发团队中培养具备威胁建模分析能力的研发人员。通过绩效考核权重(提升安全能力在研发工作中的正向考核权重)、业务主管推荐(提升安全能力在业务考核中的负向考核权重)鼓励研发人员主动申请成为威胁建模分析专员,再举行定期的安全技术培训、考试及威胁建模实战演练选出合格的威胁建模分析专员进入专家池,且对专家池中的人员每年进行能力复核和刷新,后续主要依赖专家池中的人员对Red/Orange级别的应用进行威胁建模分析和评估。
Parana公司主要依赖零信任网关(midway-auth)和基于FIDO协议的硬件token的多因素认证(MFA)确保仅合法的内部研发人员可以接入到公司内的源代码开发平台;另外通过统一权限管理平台(Bindle)动态管理研发人员与所有artifacts的访问权限确保仅授权的人员可以访问指定的内部artifacts,主要包括:
公司通过内部Code Review平台强制要求研发的每个commit在push之前都需要人工进行Peer Review,防止潜在恶意代码进入主干代码。为了实现开发的默认安全,降低已知安全风险,Parana公司花了很大力气提升开发阶段的公共安全能力:
公司禁止直接使用或者引用外部代码仓或者依赖库,使用前必须先引入内部代码仓,具体体现在以下几点:
Parana公司在代码每次编译阶段都需要经过IAST/SAST/DAST的安全测试,重要应用代码上线前还需要经过专门的渗透测试。
Parana公司的所有应用服务源代码最终都会被编译成VersionSets(即包含了所需依赖关系的代码包集合,类似于docker镜像)进行发布并交付,所有过程都是由编译引擎(Brazil)自动完成的(无人工介入),从而确保了VersionSets的完整性。研发团队自身或者其他团队需要使用这个应用只需要在自己的流水线上consume这个VersionSets即可[3]。以上这个过程,也可以使用持续交付平台(Pipelines)通过配置流水线自动化完成整个交付过程:代码push-》编译-》测试-》部署。
Parana公司使用自动化部署平台[4](Apollo)将包含微服务安装、配置、启动所需的所有信息的集合的Environments自动化部署到应用服务运行的主机组Hostclasses上。
上述这些过程同样可以通过Pipelines实现自动化安全配置(Security Config)、工作负载(workload)加固与扫描、安全补丁与漏洞修复。
Parana公司通过默认安全的开发框架引导应用服务自身进行应用、性能等日志收集与异常监控,针对潜在的安全异常要求研发团队通过公共的数据收集与融合组件(Sushi)统一上报到安全运营中心处理,同时会持续对开发人员的角色及职责与被访问代码仓关联度行为进行分析以识别潜在的软件供应链和内部威胁者(Insider Threat)等风险。
导读:DevSecOps流程的各个阶段中也面临着一些常见的威胁类型,本节将重点讲讲Parana公司的应对策略和落地措施。
综上,我们较详细地解读了Parana公司是如何构建自己的DevSecOps体系,相信对于希望构建此类体系的企业来说有一定的借鉴意义。

[1] https://apievangelist.com/2012/01/12/the-secret-to-amazons-success-internal-apis/
[2] https://docs.aws.amazon.com/whitepapers/latest/introduction-devops-aws/two-pizza-teams.html
[3] https://gist.github.com/terabyte/15a2d3d407285b8b5a0a7964dd6283b0
[4] https://www.allthingsdistributed.com/2014/11/apollo-amazon-deployment-engine.html
[5] AWS re:Invent 2015: DevOps at Amazon: A Look at Our Tools and Processes (DVO202): https://www.youtube.com/watch?v=esEFaY0FDKc
[6] DevOps Culture at Amazon: https://www.youtube.com/watch?v=mBU3AJ3j1rg
[7] Automating safe, hands-off deployments: https://aws.amazon.com/builders-library/automating-safe-hands-off-deployments/
云上攻防系列其实早在几年前笔者就公开分享过一些思路,有兴趣的可以看看Red Teaming for Cloud(云上攻防)。
众所周知,云计算领域是一个融合众多软件技术及架构的领域因此也面临着各式各样的安全威胁,作为聚焦云上攻防的蓝军从业人员(Red Team)不仅需要掌握传统领域的渗透技能,也需要积极拓展思路,切忌画地为牢。
本文是通过对近期国外TOP3云厂商已公开攻击方法的洞察分析后的阶段性总结提炼。
目前云上攻击的主要思路集中在以下几个层面:
虽然红蓝对抗机制和蓝军团队建设的经验和思考笔者已经通过不同渠道(博客、公众号、公开演讲等)多次分享了,但是今天这篇文章主要是谈一谈关于如何更好地呈现红蓝对抗的价值。
众所周知,近几年由于国家政府的重视红蓝对抗已经开始在国内各大组织和企业内蓬勃发展,但是笔者发现国内在运用红蓝对抗的价值呈现上还是有待提高的。纵观当前国内的情况,大家更重视这种形式的直接结果,如发现了几个漏洞之类的,却似乎很少公开提及如何将红蓝对抗更深次的价值呈现出来,这既包括横向上对防守团队的防御体系建设的促进,也包括纵向上对管理层的红蓝对抗价值呈现的理解。
笔者近年来一直在从事红蓝对抗机制和团队的建设,也在平时的工作中经常思考如何更好将红蓝对抗结果的价值呈现最大化,负责过蓝军建设的同学一定会或多或少被问到过类似的问题,即“红蓝对抗对企业到底有多大价值?如何量化体现?”。
一般的红蓝对抗的流程会在复盘阶段的《红蓝演练行动报告》和《复盘总结报告》中呈现红蓝对抗的结果价值,按照笔者的经验大多数情况下这两个报告一般会包括如下几方面内容:
但是这些仅仅反映了单次红蓝演练行动中发现或者暴露的问题,而大多数情况下最终会被体现为演练过程中发现了哪些漏洞的问题。对于处于红蓝对抗演练初级或者早期阶段的企业或者组织来说,或许比较能给管理层带来短暂的震撼和重视,但是经历了多次演练后就可能会面临一些“漏洞审美疲劳”的问题,诸如:
那么如何避免由于将红蓝对抗的结果呈现单纯漏洞化而导致非蓝军人员或者管理层片面地以为红蓝对抗就是找漏洞的误解,笔者认为应该从红蓝对抗的本质出发,我们都知道以攻促防是红蓝对抗的本质,因此需要蓝军从业人员懂得从方法论设计、根因分析模型、数据量化分析等维度来深度呈现红蓝对抗的价值。
首先我们来看看国外同行是如何从这几个维度来实践的。
洛克希德马丁的Kill-Chain模型就是典型的红蓝对抗的方法论,其将攻击者的思考逻辑抽象成具体的攻击步骤,指导攻击者实施攻击,同时也帮助防守者理解攻击思维。
MITRE的ATT&CK则是一个标准的根因分析模型,遵循Kill-Chain方法论通过解构攻击过程中具体的TTPs让不从事攻击的人员也可以理解攻击者思维及具体的攻击过程从而做到“知己知彼”。
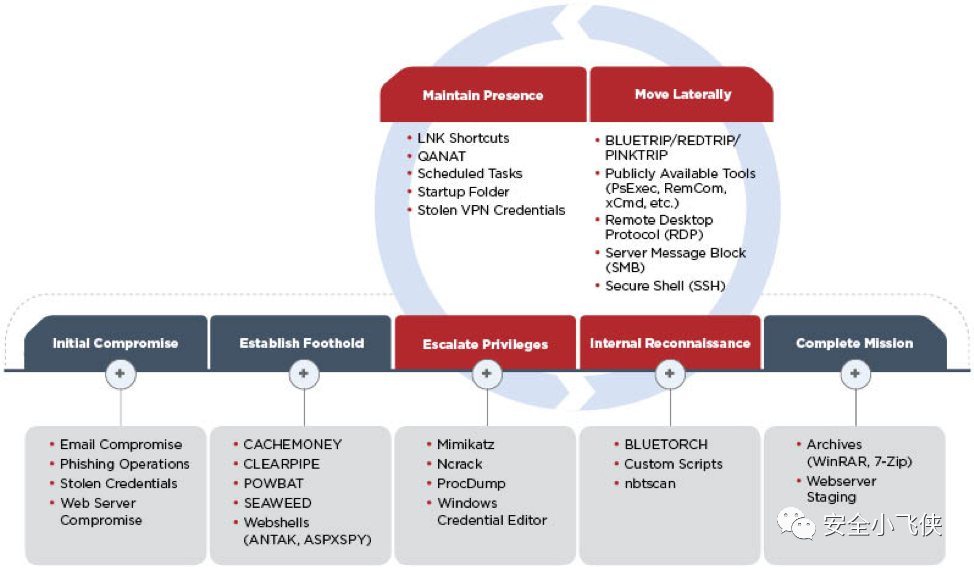
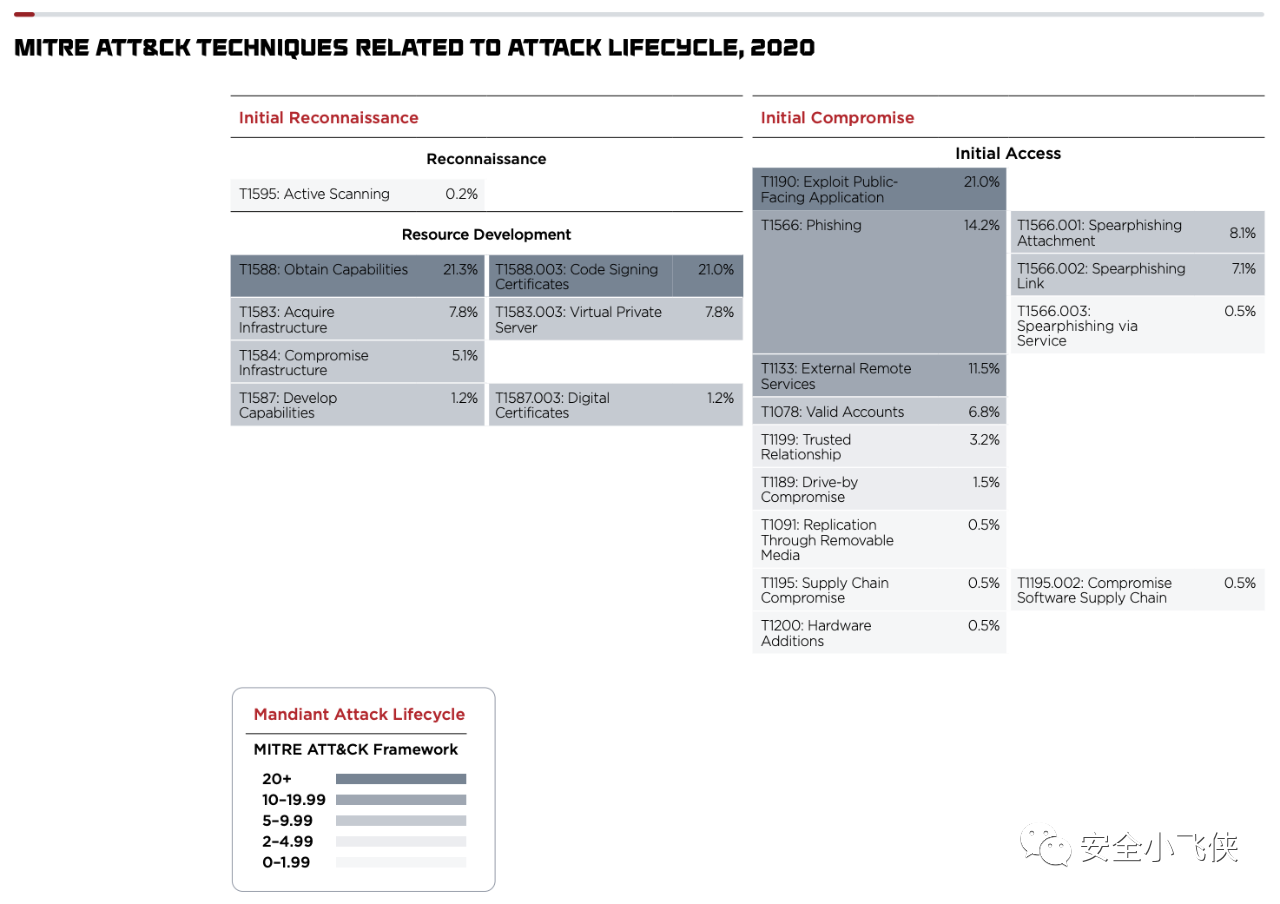
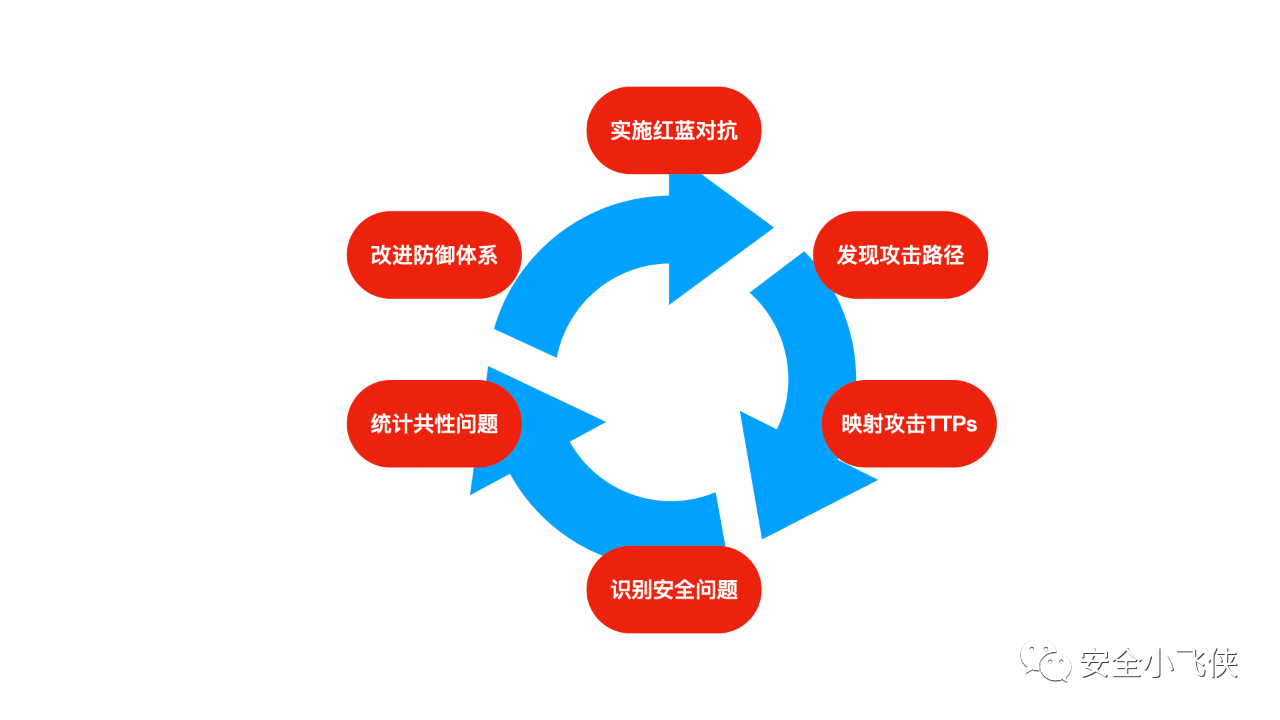

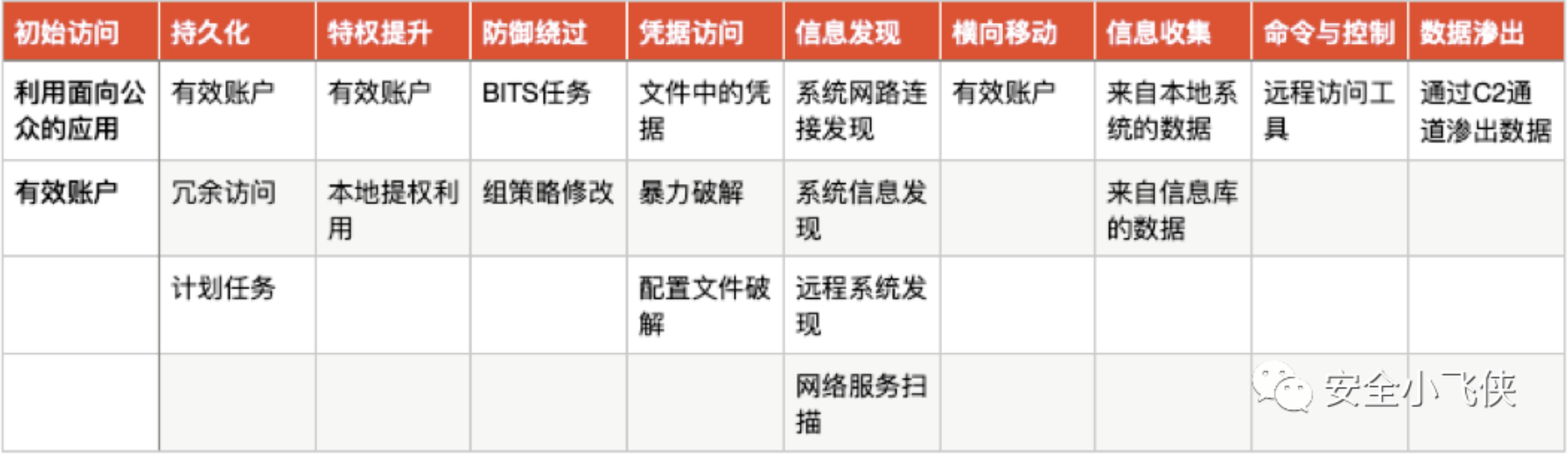
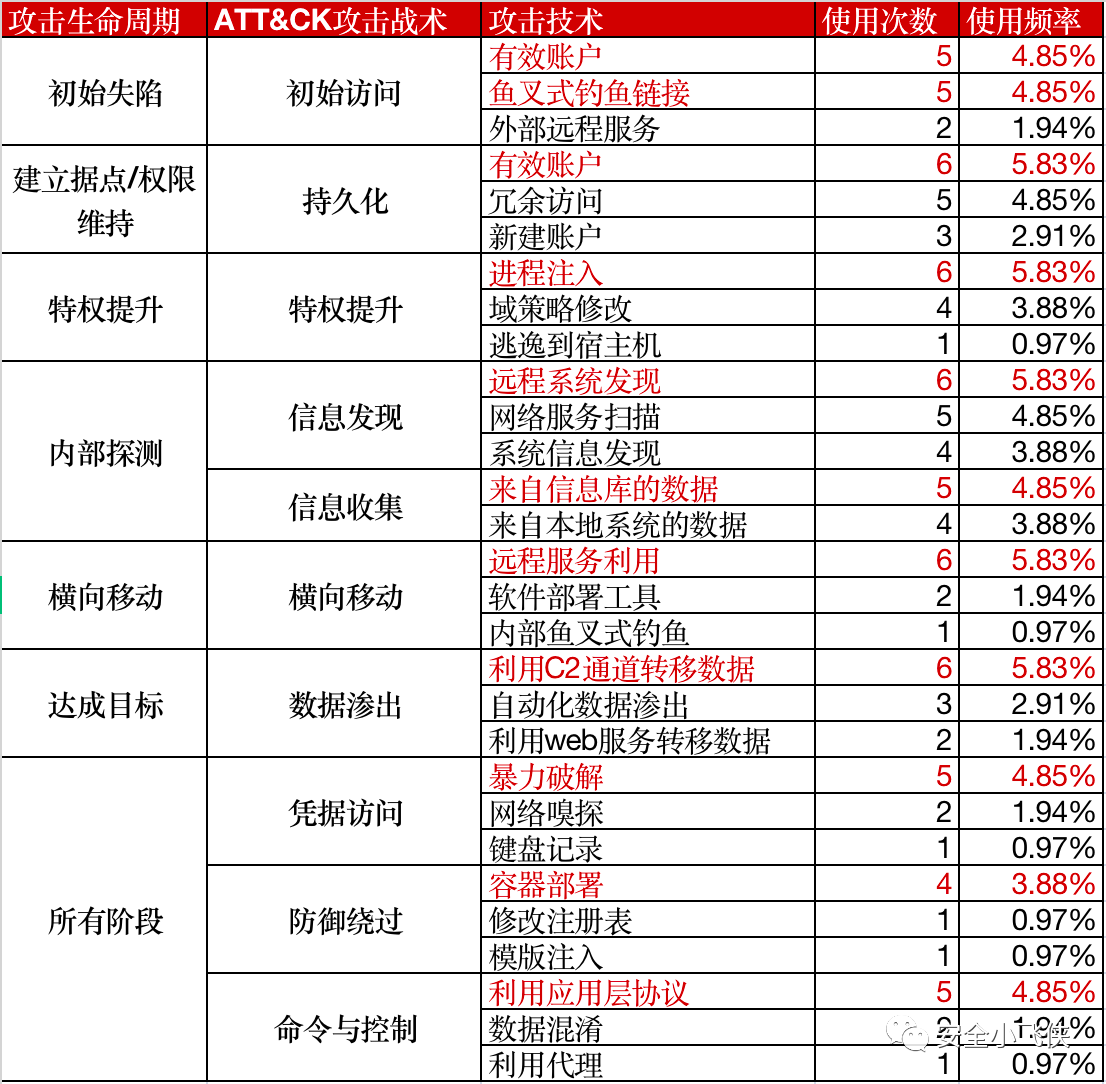
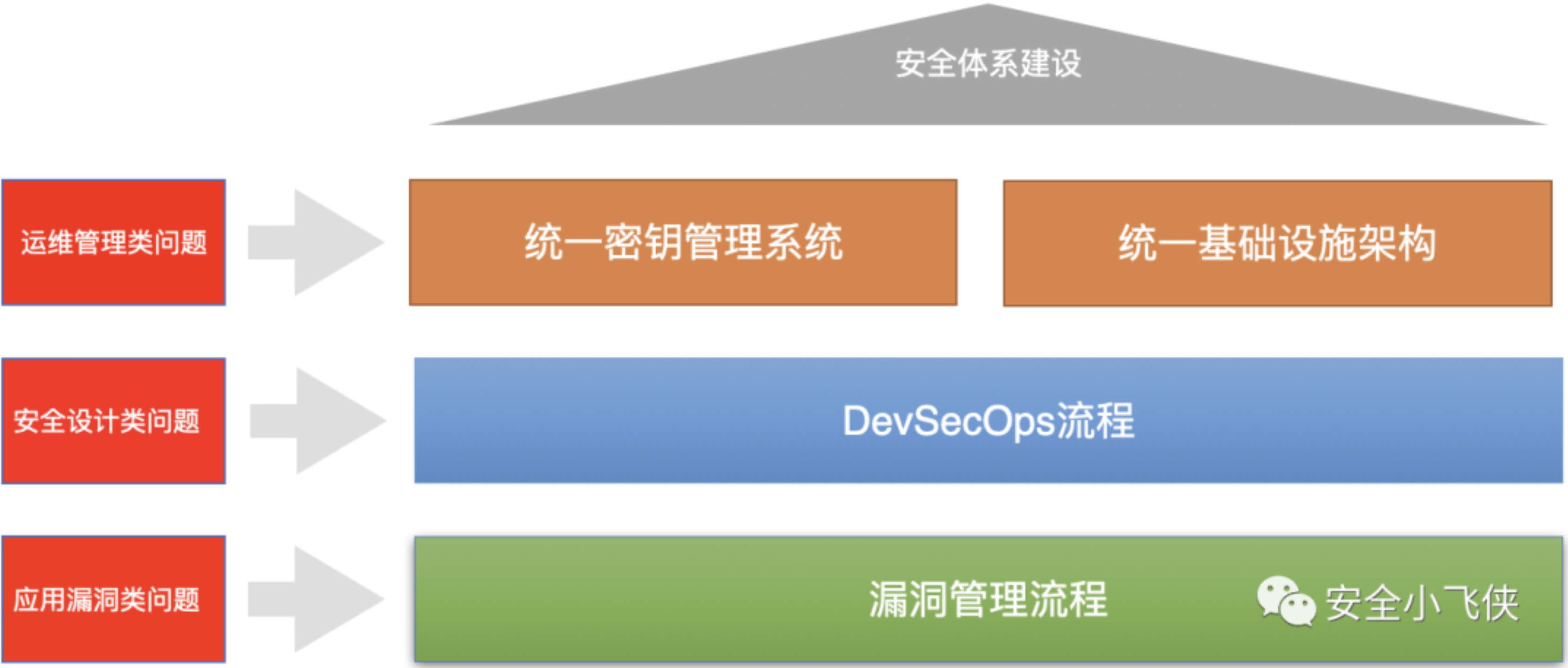
根据该模型,我们便可以建立起一个包含了方法论设计、根因分析模型及数据量化分析为一体的红蓝对抗价值呈现体系。利用这一套体系建立起横向和纵向的价值呈现标准和语言,用数据量化体现红蓝对抗的价值。